IoT Security

General Information
Title: IoT Security
Lecturer: Mohammad Hamad, Sebastian Steinhorst
Loaction: Virtual (Zoom)
Time: Each Tuesday, 14:00-16:15
Language: Lecture and tutorial in English language.
Credits: 5 ECTS credits
Duration: 3 SWS lecture
Note
Due to the ongoing COVID-19 situation, it will not be possible to conduct the lectures in the typical form in a lecture theater. Therefore, the lectures will tke place as a weekly live session via Zoom (attending lectures is required). The slides will be made available in the associated Moddle course.
Study Goals
Upon successful completion of the module, the student should be able to: (1) Explain the basic concepts of IoT (computer) security and the most common threats that threaten modern IoT systems. (2) Plan and execute pen testing for IoT systems. (3) Choose, design, and implement some protection techniques to secure IoT systems
Contents
This course focuses on the security aspects within the IoT protocol stack (i.e., data, application, and network). The course starts by looking at the IoT stack and discussing the most common IoT applications and some recent attacks against those applications. The course discusses some of the famous crypto algorithms applied to secure the (exchanged) data. Students shall implement some of these algorithms and try some techniques to break them (if possible). The course also introduces some of the authentication protocols that shall be adopted to solve some security issues in modern IoT applications. Students must implement these protocols and, later, try to break them. Attacks such as DoS and MITM are discussed in detail during the course. The students need to perform such attacks using existing tools (e.g., using Kali Linux tools) or writing their own tools. The course investigates the SSL protocol as an excellent example of securing IoT communication. Students need to integrate this protocol to ensure secure communication between smart devices. Finally, the course discusses some of the IoT software vulnerabilities and attacks which exploit these security weaknesses and how to harden the system.
Requirements (recommended)
Must: good programming skills (Python, C).
Preferable: basic knowledge of computer networking and cryptography.
Description of achievement and assessment methods
Achievement of the intended learning outcomes is assessed in a single oral exam at the end of the semester (40% of the final grade). Additionally, 2-3 assignments given during the semester are evaluated and contribute to 60% of the final grade.
Assessment criteria are:
- Ability to explain the basic security terms and attacks against the different layers of the IoT stack.
- Ability to perform basic penetration testing of IoT applications and protocols.
- Ability to define and implement some of the security mitigation mechanisms against various attacks.
IOTSEC CTF
We will not have ordinary homework or assignments in this course; instead, the students will form teams and play two locally hosted Capture The Flag (CTF) competitions. The first CTF is mainly about cryptography challenges while the second one is about attacking IoT devices. For each CTF, the teams' members need to collect flags to gain points. The students need to apply their gained knowledge to solve different challenges. Each challenge will reveal a flag once it was solved that the students can submit to prove their successful work and gain the predefined points for that challenge. The team that will collect the highest number of points during the limited time of the CTF will gain the competition.
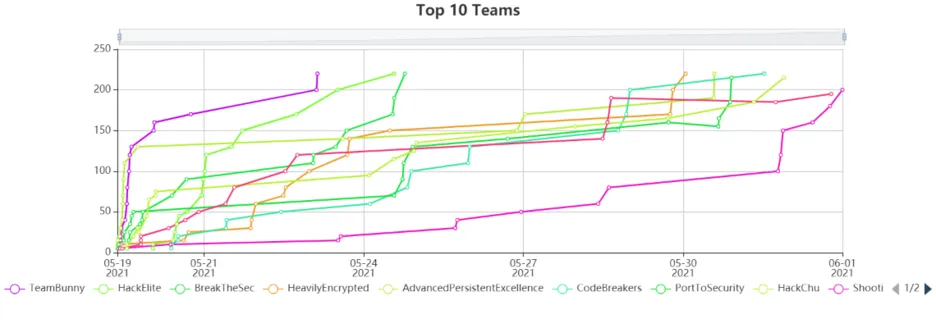
The 1st IOTSEC CTF
The winners
| Order | Team Name | Memeber 1 | Member 2 |
| 1 | TeamBunny | Milind Mathai | Paul Mierau |
| 2 | HackElite | Anoushka Udayashankar | Shivraj Hanumant Gonde |
| 3 | BreakTheSec | Ankita Kumari |
The 2nd IOTSEC CTF
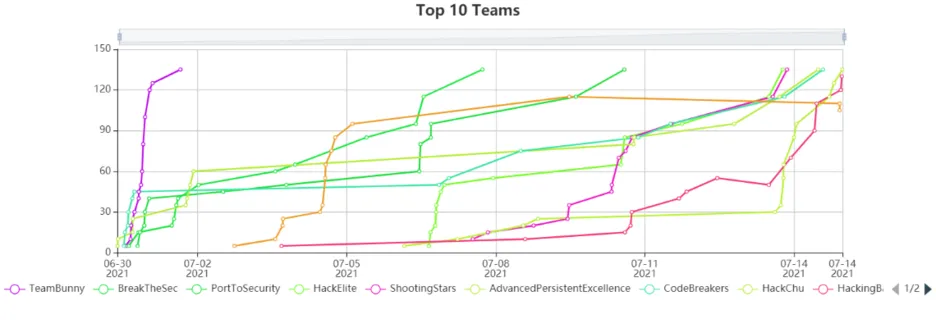
| Order | Team Name | Memeber 1 | Member 2 |
| 1 | TeamBunny | Milind Mathai | Paul Mierau |
| 2 | BreakTheSec | Ankita Kumari | Monika Singh |
| 3 | PortToSecurity | Maximilian Putz | Henrique Frutuoso |