Security and Privacy in Decentralized Systems for Data Sovereignty
Researchers: Jens Ernstberger, Jan Lauinger
Our reserach mainly focuses on the greater goal of achieving Data Sovereignty, laying the groundwork on the theoretical side, as well as providing first practical implementations of novel applications and system designs.
As such, our research focuses on (i) theory & practice of Data Sovereignty (ii) facilitating technologies for secure and verifiable computation and (iii) security and privacy challenges in facilitating infrastructure for decentralized systems.
In the following, we give a short introduction to each topic and domain.
Theory of Data Sovereignty
The concept of retaining control over sensitive or personal data can be shortly summarized as “Data Sovereignty”. Note that there exist many different notions of what “control” means in the digital world. There exist applications today that enable users to control their digital representation, these applications usually rely on an intermediary that hosts and gathers the data of its users. With our research, we specifically focus on data sovereignty that is enforced cryptographically, meaning that systems do not rely on any trusted intermediary to enforce the will of the user.
Up until today, corporations often manage user data in centralized silos. This introduces multiple issues on both the side of the service providers, as well as for users. On the service provider side, centralization attracts attackers, as minor configuration errors can lead to severe losses of user privacy, reputation and money. Further, users can only control how their data is stored and analyzed in hindsight.
In contrast, existing decentralized systems have already shown the feasibility of digital sovereignty. With the inception of Bitcoin, individuals are able to obtain financial sovereignty by performing monetary transactions without an intermediary. Ethereum further allows for programmability, enabling users to encode arbitrary and complex transaction logic beyond simple asset transfers. With this development in mind, we research how existing and future systems can build upon previous work to enable digital sovereignty beyond financial assets.
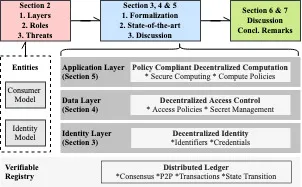
In our work "SoK: Data Sovereignty" (find reference below), we identity decentralized identity, decentralized access control, and policy-compliant decentralized computation as core building blocks if systems should achieve a strong notion of data sovereignty for their users. Our research aims to enhance efficiency, security, privacy, and verifiability of aforementioned topic domains. We now present our topic scopes in more detail.
Decentralized Identity
Decentralized Identity aims to provide the technical foundations to eliminate the shortcomings of centrally managed digital identities. A system for decentralized identity ensures that (i) digital identities can be maintained without a centralized entity, and that (ii) a user can authenticate without relying on a third party. A decentralized identity provides a solution to both challenges through decentralized identifiers and publicly verifiable credentials. With publicly verifiable credentials, users can decide what information is shared to requesting third parties.
Decentralized Access Control
Decentralized access control intends to remove the reliance of users on centralized access controllers. In Web 3.0, decentralized access control should allow users to verifiably control who gets access to personal data. As such, users should be able to conditionally control access based on presented credentials, token ownership or Decentralized Autonomous Organization (DAO) membership.
Policy-compliant Decentralized Computation
We argue that the gap between how Web 3.0 applications are envisioned, and how Web 2.0 applications are currently operating, demands for a novel description of user-governed computation. To account for this dichotomy, we propose the notion of PCDC, which allows users to govern the execution of arbitrary external programs. PCDC enables a new class of protocols, where users put their data to use whilst obtaining previously unattainable guarantees for privacy and computational correctness. To achieve privacy and protect data beyond access, PCDC relies on secure computation. The data consumer therefore only observes the result, whereas the personal data, which is used as an input, can only be observed by the user.
Data Sovereignty in Practice
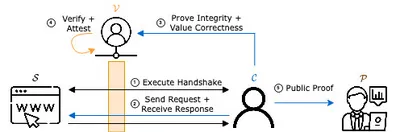
Users increasingly entrust web applications with their most sensitive data. By relying on secure channels, users can communicate with web applications to enable advanced online services. However, data exchanged and received is only integrity protected with respect to the participants in the secure channel. For example, a user can link its bank account to on line payment systems, such as PayPal, to send and receive money with increased fraud prevention. Once linked, users can interact with web applications that support online payments via PayPal. When a payment is made, the PayPal API is invoked and an HTTP request containing the payment information is sent. Once completed, the user is notified that the payment has succeeded. However, a user is unable to prove to any third party that the payment has indeed succeeded.
As a response, we developed Origo, a novel TLS oracle which relies on the verifier acting as a proxy between the client and the server. This solution incurs a trade-off between security and performance, and due to significantly enhanced performance is extremely relevant in embedded systems and IoT. The data transmitted between any client and server can be non-interactively proven towards a smart contract, and translated into an on-chain credential by the client without any further entity's interference - effectively liberating any data belonging to the client.
Secure & Verifiable Computation
Our research touches upon advanced cryptographic techniques which we introduce shortly.
Secure Computation
Secure computation allows two mutually distrusting parties to jointly compute a public function without learning the input of other parties. Parties which participate in secure computation protocols usually receive the function output which ideality does not reveal anything about any inputs of the function. There exist multiple techniques for secure computation, which we introduce next.
- Trusted enclaves or trusted execution environments depend special hardware to achieve secure computation. Trusted enclaves are centralized computing environments but achieve the best computing performance compared to other secure computation technologies. When designing secure protocols, trusted enclaves guarantee execution integrity, remote attestation, and secure computation but in reality, different kinds of attacks (e.g. side channel attacks) exist.
- Multi-party computation or MPC achieves secure computation by solely relying on cryptographic constructions. MPC is a broad research area which comes in many flavours (e.g. two-party secure computation, three-party secure computation, etc.) and can be constructed for different security guarantees (e.g. security for a setting with a honest majority, dishonest majority, two-thirds honest majority, etc.). Further, MPC settings assume semi-honest parties which follow the imposed protocol specification or even provide security against malicious parties which arbitrarily deviate from the protocol specification. The computation performance of MPC typically scales with the number of participants and can achieve a decent notion of decentralization.
- Homomorphic Encryption of HE exist as fully or partial homomorphic encryption, where fully homomorphic encryption can be used to compute arbitrary functions (multiplications and additions). HE is another large research area and represents a very neat solution to secure computation. However, even though great improvements have been achieved as of today, HE often counts as impractical due to to complex performance requirements.
Currently, our research touches upon MPC and specifically, two-party secure computation or 2PC. Multiple approaches to compute a function in 2PC exist and modern systems build general-purpose 2PC by relying on complex compilation pipelines. If you are interested in conducting research in the area of 2PC, please email jan.lauinger@tum.de.
Benchmarking Zero Knowledge Proofs
Cryptographic proofs play a fundamental role in complexity theory and cryptography. They enable an untrusted prover to issue a guarantee to a verifier that it performed a certain computation correctly. Further extensions of this concept even allow the prover to work in zero-knowledge meaning that the proof reveals no additional information to the verifier beyond the truthfulness of the statement. In the past decade, general-purpose Zero Knowledge Proofs have made the jump from theory to practice and are nowadays a core component of many such trust-minimized systems providing integrity (such as digital signatures, verifiable computation, or verifiable storage), privacy (such as mixers, e-cash, privacy coins, or anonymous credentials), and scalability (such as rollups, bridges, or light clients).
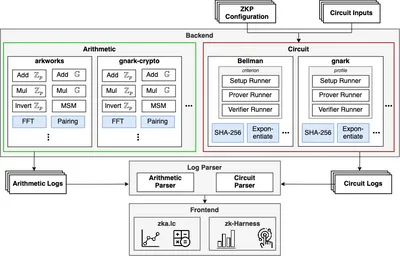
However, measuring the performance of concrete implementations remains difficult, due to the vast amount of libraries being developed concurrently, and the transcending domain knowledge required. Hence, we developed zk-Bench, an extensible benchmarking framework for low-level arithmetics and general purpose Zero Knowledge Proofs, which facilitates and eases the comparison of different implementations and uncovers important trade-offs.
Security & Privacy of Decentralized Systems
Blockchain Censorship
Permissionless blockchains promise to be resilient against censorship by a single entity. This suggests that deterministic rules, and not third-party actors, are responsible for deciding if a transaction is appended to the blockchain or not. In 2022, the U.S. Office of Foreign Assets Control (OFAC) sanctioned a Bitcoin mixer and an Ethereum application, putting the neutrality of permissionless blockchains to the test.
In response, we provide a definition of censorship for blockchains, capturing various system layers, and temporal features. We dissect the quantitative extent of censorship performed by Ethereum smart contracts, block builders, block proposers, and block relayers. We further provide quantitative evidence of the historical transaction confirmation latency on Ethereum. We find that Ethereum’s move to PoS and Proposer-Builder Separation (PBS) has delayed the inclusion of both censored and non-censored transactions. E.g., the average inclusion delay for TC transactions increased from 15.8 ± 22.8 seconds in Aug. 2022 to 29.3 ± 23.9 seconds in Nov. 2022. Increased confirmation latencies exacerbate sandwich attack risks. We prove that no PoS (PoW) protocol can achieve censorship-resilience, if the censoring validators (miners) make up more than 50% of the validator committee (hashing power).
Publications & Other Resources
2023
- "zk-Bench: A Toolset for Comparative Evaluation and Performance Benchmarking of SNARKs", TBP
- "Proving Provenance of Sensitive Data", TBP
- "Blockchain Censorship", PDF
- “SoK: Data Sovereignty”, PDF
- "Anonymous Domain Ownership", PDF
2021
- "A-PoA: Anonymous Proof of Authorization for Decentralized Identity Management", PDF
Open-Source Software & Resources