Post-Quantum Cryptography
Contact: Patrick Karl, Jonas Schupp
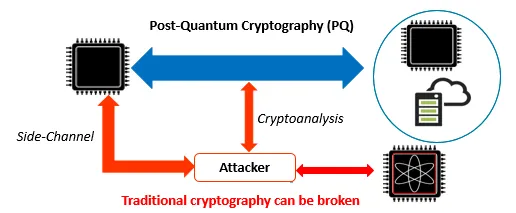
In recent years, the market for the Internet of Things (IoT) has rapidly grown. Public-key cryptography builds the basis for a secure communication between different devices. However, the fast progress in the development of quantum computers is leading to an increasing concern about the security of current communication systems. Practical quantum computing algorithms will be able to break most of the public-key cryptosystems in use, including Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC). In contrast to traditional cryptography, Post-Quantum Cryptography relies on different mathematical hard problems which are believed to be secure against quantum attacks. Post-Quantum Cryptography can be divided into four different main classes: Hash-based Cryptography, Isogeny-based Cryptography, Code-based Cryptography, and Lattice-based Cryptography.
In our research, we focus on secure and efficient HW/SW implementations of Post-Quantum Cryptography and analyze their vulnerability to side-channel attacks in order to provide efficient countermeasures.
The focus of our research lies in the following fields:
- Side-channel attacks and development of countermeasures with a focus on Code-based and Lattice-based Cryptography
- Efficient implementations of Lattice-based signatures through HW/SW Codesign
Selected Publications
Hamburg, Mike and Hermelink, Julius and Primas, Robert and Samardjiska, Simona and Schamberger, Thomas and Streit, Silvan and Strieder, Emanuele and van Vredendaal, Christine: Chosen Ciphertext k-Trace Attacks on Masked CCA2 Secure Kyber, IACR Transactions on Cryptographic Hardware and Embedded Systems 2021 (CHES)
Schamberger, Thomas; Renner, Julian; Sigl, Georg; Wachter-Zeh, Antonia: A Power Side-Channel Attack on the CCA2-Secure HQC KEM. Smart Card Research and Advanced Applications 2020 (CARDIS)
Fritzmann, Tim and Sepulveda, Johanna: Efficient and Flexible Low-Power NTT for Lattice-Based Cryptography. In 2019 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST)
Schamberger, Thomas and Mischke, Oliver and Sepulveda, Johanna: Practical Evaluation of Masking for NTRUEncrypt on ARM Cortex-M4. Constructive Side-Channel Analysis and Secure Design, Springer International Publishing, 2019 Constructive Side-Channel Analysis and Secure Design 2019 (COSADE)
Fritzmann, Tim and Sharif, Uzair and Müller-Gritschneder, Daniel and Reinbrecht, Cezar and Schlichtmann, Ulf and Sepulveda, Johanna: Towards Reliable and Secure Post-Quantum Co-Processors based on RISC-V. Design, Automation & Test in Europe (DATE) 2019, 2019 Florence, Italy
Braun, Konstantin and Fritzmann, Tim and Maringer, Georg and Schamberger, Thomas and Sepulveda, Johanna: Secure and Compact Full NTRU Hardware Implementation. 26th IFIP/IEEE International Conference on Very Large Scale Integration (VLSI-SoC), 2018 Verona, Italy
Fritzmann, Tim and Pöppelmann, Thomas and Sepulveda, Johanna: Analysis of Error-Correcting Codes for Lattice-Based Key Exchange. Conference on Selected Areas in Cryptography (SAC), 2018 Calgary, Canada, 1-22